The data economy’s landscape presents novel opportunities and challenges. Prominent corporations that specialize in software & hardware services engage in intricate data mining operations, collecting vast user information that underpins their services and business models. Amid their undeniable influence, concerns emerge about the implications of their data-driven approaches.
The ethical dimensions of data dynamics have come under scrutiny. Advanced algorithms and substantial computing power enable these entities to subtly influence user behaviors and choices, highlighting the intricate power dynamics in today’s digital world.
As society becomes more interconnected and reliant on these tech entities, understanding their data practices gains importance. This overview delves into the intricate facets of the data economy, exploring how strategies employed by significant players may mold our digital experiences and interactions.
The internet, a cornerstone of modern society, has revolutionized the way we communicate, learn, and conduct business. However, this powerful tool in its present state has significant flaws.
The most pressing issue facing our current internet infrastructure revolves around the delicate balance between accountability and preserving individual freedoms. As efforts to combat misinformation and ensure online safety intensify, concerns over censorship, free speech, and privacy violations have emerged as significant points of consideration for state & federal legislators.
Our free-market is resisting addressing this failure, because it would undercut the existing advantages of their operating business models, putting shareholder value at risk.
In the realm of internet regulation, liberal-minded entrepreneurs, academics, and politicians emphasize the urgency of addressing the spread of misinformation and privacy concerns. They view misinformation as a threat to public well-being and advocate for measures to ensure the accuracy of online information.
Conversely, conservative-minded entrepreneurs, social leaders, and politicians are cautious about increased centralization of control and potential biases of governing parties. They highlight the importance of maintaining individual freedoms in the online space while safeguarding against undue concentration of power. Striking a balance between tackling misinformation and preserving internet openness remains a challenge that both factions grapple with.
As data infrastructure becomes more standardized and cost-effective, and large software companies run out of customers for their existing product suites, it is driving a convergence of tooling among software providers. Simultaneously, Web3 technologies are emerging, offering a solution to data control issues by enabling user data ownership. This challenges companies whose value is built on data silos and opens up the opportunity for a democratic form of AI governance that address the concerns of legislators and citizens alike. Considering the importance of up-to-date data for predictive AI systems, open-source decentralized AI will likely dominate as users seek privacy-focused environments.
In a nutshell, Smart Wallets represent the upcoming frontier in software markets, but not as you’ve known them to date. No, these Smart Wallets will be cryptographically secure 1st party data vaults facilitate decentralized computing environments, akin to comprehensive apps like WeChat. In this evolving landscape, a business’s brand reputation will emerge as its only differentiator and competitive advantage.
We envision the internet’s future as a peer-to-peer encrypted mesh, where users retain ownership of their metadata’s value and collaborate within a democratically governed information network. This vision contrasts with the current advertising-driven economy and other sectors using data science to profit from people’s online behaviors and digital identities.
Our belief stems from the potential of a decentralized AI system to accumulate a more extensive dataset compared to private data silos. For this outcome to prevail, a compelling reason to adopt such infrastructure is essential. This infrastructure prioritizes both decentralized onboarding verification of digital identity and the preservation of individual freedoms. The core principles are freedom and accountability, all underpinned by a common-sense architecture.
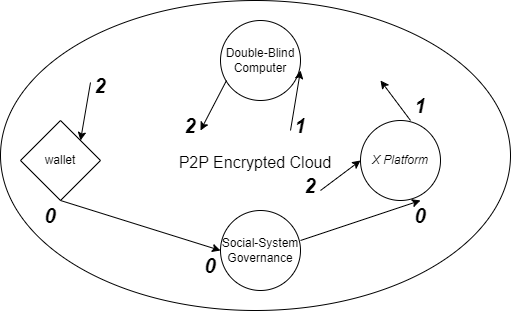
In Figure 1. a wallet module makes a request [0] to x platform to use an app, AI, or view content, and that request is routed [0] through the social-system governance to authenticate the user, platform, and requested function; assuming access is adequately permissioned the request passes to x platform [0]. X platform logs the request to its system [1], triggering a request to the double-blind computer [1]. The double-blind computer [2] processes the triggered request, sending outputs directly to the originating wallet [2], while x platform [2] receives functional outputs & aggregate insights in parallel.
Similar to the user permissions and authentication systems within traditional software products, our proposal introduces a decentralized abstraction of this concept, that’s functional dynamism allows it to meet the needs of a scale composable data architecture; a user-centric network.
This abstraction serves as the foundation for constructing governable, shared information space. In this decentralized model, the verification of personhood is distributed and fortified through collaborative efforts involving multiple parties distributed between the physical and digital domain. These parties rely on community reputation, which aggregates private reputational scores from the user base.
Additionally, this approach factors in content, products, and services, establishing a natural mechanism for aligning values between individuals and communities by using distributed electoral processes to install accountable operators to manage the oversight of various domain and functional silos by their community of peers.
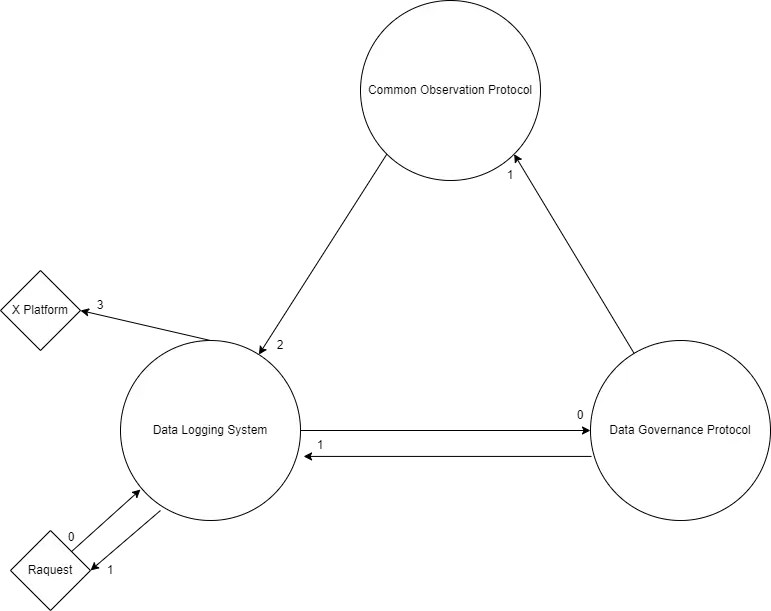
In Figure 2. a wallet or platform makes a request [0] for data to view, a model to manipulate data, or a series of transformations on a piece of data. That request is logged to the Data Logging System [0] using homomorphic encryption to the peer to peer encrypted logging mesh and then routed to the [0] Data Governance Protocol. Depending on the permissions available to the party making the request (wallet or platform) the request [1] is either denied, with the denial record being sent [1] to the Data Logging System before being sent back to the requesting party; or the request [1] is routed to the Common Observation Protocol. The Common Observation Protocol [2] maps the locations of all the required knowledge (functional data transformation definitions, or current data states or aggregations) from the peer to peer encrypted logging mesh, sending [2] the transaction payload to be recorded back on the Data Logging System. The successful logging of a transaction payload [2] from the Common Observation Protocol routes [3] the payload to x platform to enable request transactions to be executed.
Double-blind computation, powered by fully homomorphic encryption, stands as a groundbreaking advancement with immense potential for ethical, scientific pursuits. By enabling computations on encrypted data without decryption, this approach ensures heightened privacy and data security. Users and software providers can collaborate and analyze sensitive information without exposing the actual data, thus safeguarding individual privacy and confidential details.
This innovation reverberates across a spectrum of scientific endeavors. Medical research can thrive by securely analyzing patient data without compromising privacy. Financial analyses can be conducted without revealing sensitive financial records. Collaborative efforts in various fields can flourish, empowered by the assurance of privacy. Ultimately, double-blind computation with fully homomorphic solutions brings us closer to a future where ethical science-driven initiatives harness the potential of data analytics while upholding individual privacy and data protection.
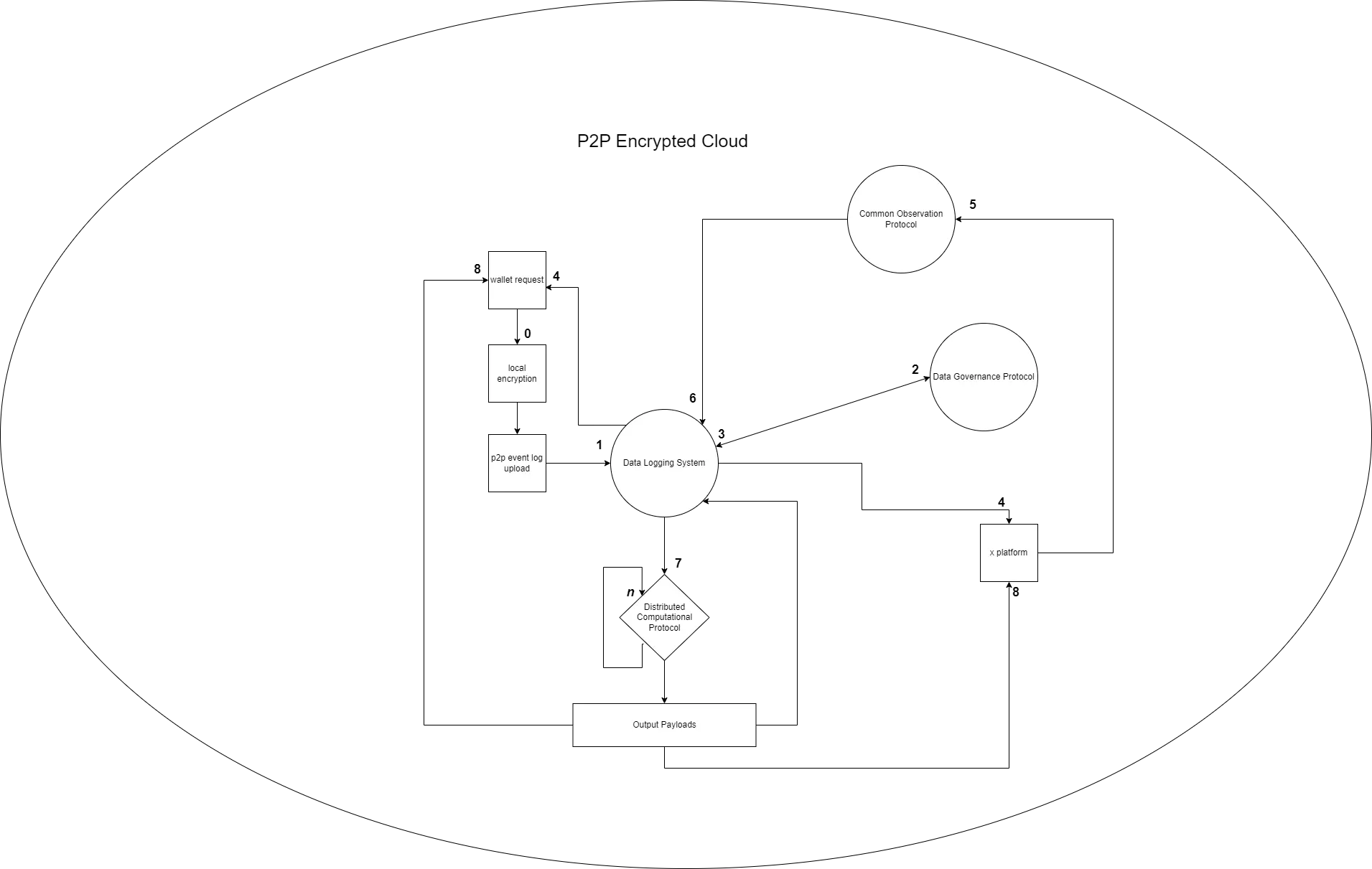
In Figure 3. a wallet request occurs when a singular data point changes state [0], which leads to the wallet’s local key utilizing fully homomorphic encryption over the data, and the logging that payload as a request in the P2P Encrypted Cloud via the Data Logging System [1]. The Data Logging System takes the received record routing it [2] to the Data Governance Protocol to verify the transaction permissions and back to the Data Logging System [3]. If the transaction is complete, then the Data Logging System updates the state of the request to reflect that to the P2P Encrypted Cloud, delivering the notice back to the originating wallet [4]; the same is true if permissions are denied.
If the state change request contained functional transformation requests, the Data Logging System routes the authorized request to X platform [4], which will utilize the Common Observation Protocol to build the functional payload and data map [5], before returning the robust request to the Data Logging System [6] to be executed.
The Data Logging System, with the new enriched transaction request, sends the executable to the Distributed Computational Protocol [7], where it loops through the executables until all required functional transformations [n] have been performed on the homomorphically encrypted payloads. These outputs are registered to the P2P Encrypted Cloud and delivered as 2 separate messages to the wallet & x platform independently [8].
$paypr is the native utility token of the COMMON SENSE PROTOCOL and will be redeemable across its entire environment. Our plan is to sell 39% of it OTC over the next four years as we onboard our customers to pay for their software.
111T tokens pre-mined will be earned via Engage-2-Earn, Pool-2-Earn, data mining platforms owned by the protocol, or purchased on various exchanges within the Solana network.
The goal is to begin issuing new tokens in 2028 at an inflation rate inverse the error rate of our networks decentralized AI system; allowing it to be inflationary or deflationary depending on future outcomes.
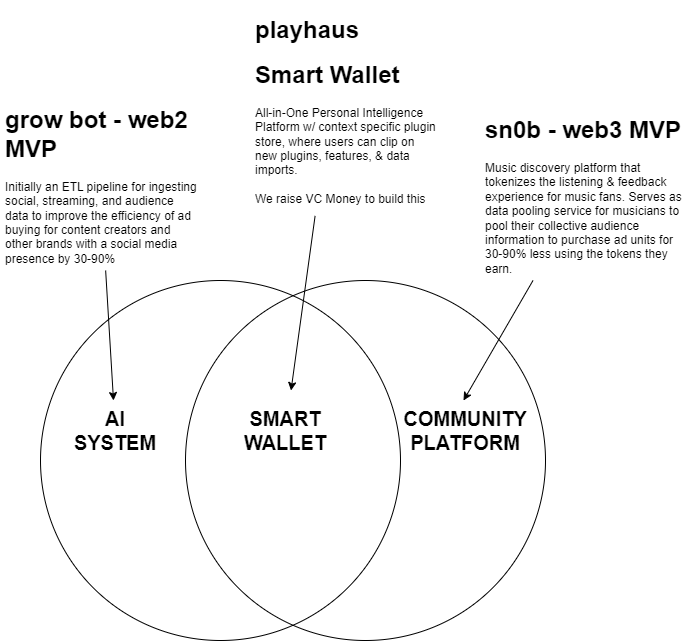
Creating a decentralized information structure poses a significant challenge that necessitates a unified language to maintain data integrity and ethical considerations across diverse contexts. This common framework ensures consistency in data interpretation and usage. Moreover, engaging community stakeholders from the outset is crucial. Their involvement helps align the structure with real-world needs, ensures ethical practices, and fosters a sense of ownership. Ultimately, a decentralized information structure built with a shared language and inclusive collaboration promises to navigate complexities while upholding data integrity, ethics, and relevance. Join our community to help shape the future of this public utility, or check out our Road Map to learn more.
Heart&SOL is a daily newsletter at the intersection of AI, cryptography, and online culture.
Be first to the future.